NetSetMan
NetSetMan
NetSetMan is a network settings manager that helps you switch between 6 different, visually structured profiles that includes IP address, subnet mask, default gateway, preferred/alternate DNS server, computer name, workgroup, DNS domain, WINS server, default printer and run scripts. Although mostly for mobile users who have multiple network settings at home, office, wireless, etc, this software can also be useful for advanced network configuration and diagnostics.
Download and Source
-Saba
NetSetMan is a network settings manager that helps you switch between 6 different, visually structured profiles that includes IP address, subnet mask, default gateway, preferred/alternate DNS server, computer name, workgroup, DNS domain, WINS server, default printer and run scripts. Although mostly for mobile users who have multiple network settings at home, office, wireless, etc, this software can also be useful for advanced network configuration and diagnostics.
Download and Source
-Saba
Posted on Saturday, November 03, 2012
Awesome Duplicate Photo Finderv1.1
Awesome Duplicate Photo Finderv1.1
Awesome Duplicate Photo Finder is a powerful tool that helps you to find and remove duplicate photos or similar pictures on your PC. It is able to compare pictures that were resized or with corrected colors (e.g. contrast modified, black and white photos, etc.)
Posted on Saturday, November 03, 2012
DataRecoveryv2.4.7UPDATED
DataRecoveryv2.4.7 UPDATED
-Saba
Posted on Saturday, November 03, 2012
HOWTO : SQLi Lab Series
HOWTO : SQLi Lab Series
The
following is the SQLi Lab, which is created by Audi-1 who is an Offensive
Security Certified Expert (OSCE). He explains how SQLi works.
SQLi Lab Series - Introduction
SQLi Lab Series - Error Based
SQLi Lab Series - Double Query / SubQuery
SQLi Lab Series - Blind Injection - Boolean Based
SQLi Lab Series - Blind Injection - Time Based
SQLi Lab Series - Using Outfile / Dumpfile
SQLi Lab Series - Post Based
SQLi Lab Series - Double Query
SQLi Lab Series - Update Query
SQLi Lab Series - Insert Query / Headers
SQLi Lab Series - Cookie Based
Second Order Injection
The whole series of the video of SQLi Lab Series
SQLi Lab Series - Introduction
SQLi Lab Series - Error Based
SQLi Lab Series - Double Query / SubQuery
SQLi Lab Series - Blind Injection - Boolean Based
SQLi Lab Series - Blind Injection - Time Based
SQLi Lab Series - Using Outfile / Dumpfile
SQLi Lab Series - Post Based
SQLi Lab Series - Double Query
SQLi Lab Series - Update Query
SQLi Lab Series - Insert Query / Headers
SQLi Lab Series - Cookie Based
Second Order Injection
The whole series of the video of SQLi Lab Series
Posted on Saturday, November 03, 2012
Anonymous-DoS
Anonymous-DoS
an anonymous dedicated http flood program
Description
What is Anonymous-DoS?
Anonymous-DoS is a http flood program written in hta and javascript, designed
to be lightweight, portable, possible to be uploaded to websites whilst still
having a client version, and made for Anonymous ddos attacks.
How does it work?
It will flood a chosen web server with HTTP connections, with enough it will
crash the server, resulting in a denial of service.
Anonymous-DoS is a http flood program written in hta and javascript, designed
to be lightweight, portable, possible to be uploaded to websites whilst still
having a client version, and made for Anonymous ddos attacks.
How does it work?
It will flood a chosen web server with HTTP connections, with enough it will
crash the server, resulting in a denial of service.
Posted on Saturday, November 03, 2012
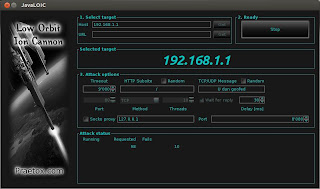
Java LOIC Beta
Java LOIC
BetaDescription
JavaLOIC is a clone of LOIC written entirely in java.
This project is not related with Praetox.
This project is not related with Praetox.
Posted on Saturday, November 03, 2012
XOIC is a tool to make (D)DoS attacks.
XOIC
XOIC is a tool to make (D)DoS attacks.
Description
XOIC is a tool to make DoS attacks.
More information about DoS attacks: http://de.wikipedia.org/wiki/Denial_of_Service.
The tool makes a (D)DoS attacks to any IP address,with a user selected port and a user selected protocol.
XOIC is in my tests a little more powerful as loic (low orbit cannon).
The reason is that I've left out gadget devastating performance (eg request counter and TCP HTTP UDP Icmp message) and other things.
XOIC have 3 modes:
-Test Mode
-Normal DoS attack mode (No request counter and TCP HTTP UDP ICMP message because of performance )
-DoS attack with a TCP/HTTP/UDP/ICMP Message
THIS IS THE NEW DLR_DoS -> XOIC
Only for win7 and win8!!!
Use it at your own risk!
Use this tool only to test your server!
WARNING:
Never use it to attack servers that you don´t own or have permission by the owner !
Tags: XOIC , xoic , loic , DoS attack programm , loic
XOIC Web SiteMore information about DoS attacks: http://de.wikipedia.org/wiki/Denial_of_Service.
The tool makes a (D)DoS attacks to any IP address,with a user selected port and a user selected protocol.
XOIC is in my tests a little more powerful as loic (low orbit cannon).
The reason is that I've left out gadget devastating performance (eg request counter and TCP HTTP UDP Icmp message) and other things.
XOIC have 3 modes:
-Test Mode
-Normal DoS attack mode (No request counter and TCP HTTP UDP ICMP message because of performance )
-DoS attack with a TCP/HTTP/UDP/ICMP Message
THIS IS THE NEW DLR_DoS -> XOIC
Only for win7 and win8!!!
Use it at your own risk!
Use this tool only to test your server!
WARNING:
Never use it to attack servers that you don´t own or have permission by the owner !
Tags: XOIC , xoic , loic , DoS attack programm , loic
Categories
Features
- Normal DoS attack mode. (TCP/HTTP/UDP/ICMP)
- Testmode will show you how many seconds you Computer needs for 10000 requests.
- DoS attack with a TCP/HTTP/UDP/ICMP message
- GUI and easy to use!
Posted on Saturday, November 03, 2012
jsql-injection
An easy to use SQL injection tool for retrieving database informations from a distant server.
You can discuss about jSQL Injection on the discussion group.
jSQL Injection features:
- GET, POST, header, cookie methods
- normal, error based, blind, time based algorithms
- automatic best algorithms detection
- data retrieving progression
- proxy setting
- evasion
.png)
For now supports MySQL.
Running injection requires the distant server url and the name of the parameter to inject.
If you know an injection should work but the jSQL tool doesn't access the database, you can inform me by email or use the discussion group.
For a local test, you can save the following PHP code in a script named for example simulate_get.php, and use the URLhttp://127.0.0.1/simulate_get.php?lib= in the first field of the tool, then click Connect to access the database:
<?php mysql_connect("localhost", "root", ""); mysql_select_db("my_own_database"); $result = mysql_query("SELECT * FROM my_own_table where my_own_field = {$_GET['lib']}") # time based or die( mysql_error() ); # error based if(mysql_num_rows($result)!==0) echo" true "; # blind while ($row = mysql_fetch_array($result, MYSQL_NUM)) echo join(',',$row); # normal ?>
Posted on Saturday, November 03, 2012
LastActivityView is a tool for Windows
LastActivityView is
a tool for Windows operating system that collects information from various
sources on a running system, and displays a log of actions made by the user and
events occurred on this computer.
Posted on Saturday, November 03, 2012
The Biggest Problem in Computer Security
The Biggest Problem in Computer Security
People tend to focus on various areas as being important for
computer security such as memory corruption vulnerabilities, malware, anomaly
detection, etc. However the lurking and most critical issue in my opinion is
staffing. The truth is, there is no pool of candidates out there to draw from
at a certain level in computer security. As an example, we do a lot of
consulting, especially in the area of incident response, for oil & gas,
avionics, finance, etc. When we go on site we find that we have to have the
following skills:
1. Soft skills. (often most important) The ability to talk
to customers, dress appropriately, give presentations or speak publicly, assess
the customer staff, culture and politics, and determine the real goals. I can't
stress enough how important this is. It's not the 90s anymore, showing up with
a blue mohawk, a spike in the forehead and leather pants, not a team player,
cussing and surfing porn on the customers system doesn't cut it no matter how
good you are technically. If you are that guy then you get to stay in the lab
and I guarantee you will make far less money. Even if you can write ASLR bypass
exploits and kernel rootkits.
Posted on Saturday, November 03, 2012
How to Prevent Security Breaches from Known Vulnerabilities
How to Prevent Security Breaches from Known Vulnerabilities
While it's bad to be targeted by a hacker using new and relatively unknown security vulnerabilities, it's awful to fall victim to well-known attacks.
Posted on Saturday, November 03, 2012
I2P ANONYMOUS NETWORK
I2P ANONYMOUS NETWORK
I2P is an anonymizing network, offering a simple layer that identity-sensitive applications can use to securely communicate. All data is wrapped with several layers of encryption, and the network is both distributed and dynamic, with no trusted parties.
Many applications are available that interface with I2P, including mail, peer-peer, IRC chat, and others.
Posted on Saturday, November 03, 2012
The Chakra Project !
The Chakra Project !
Chakra GNU/LInux is a free, user-friendly and extremely powerful liveCD and distribution using the award winning KDE SC and Plasma Desktop with a bundle system to use GTK-apps.
Posted on Saturday, November 03, 2012
ESSPEE - Penetration Testing & Forensics
ESSPEE - Penetration Testing & Forensics
ESSPEE is a derivetive of Back | Track 5, based on Ubuntu 12.04. Designed for users who wish to use only free software. It is packed with featured security tools with stable configurations. This version consolidates the Unity desktop interface; a brand new way to find and manage your applications.
Thanks to Back Track, Blackbuntu, CAINE and DEFT for inspiration.
Being a sole developer to this distro, I wish it could help Open Source community with a better interface for Penetration testing and Forensics. I really enjoyed my work for last six months.
Please let me know about bugs and if possible provide solution also.
So finally, "This is the season of roses and wine, this moment is yours....Just live it up !!!"
Thanks again.
ESSPEE - Penetration Testing & Forensics Web SiteThanks to Back Track, Blackbuntu, CAINE and DEFT for inspiration.
Being a sole developer to this distro, I wish it could help Open Source community with a better interface for Penetration testing and Forensics. I really enjoyed my work for last six months.
Please let me know about bugs and if possible provide solution also.
So finally, "This is the season of roses and wine, this moment is yours....Just live it up !!!"
Thanks again.
Posted on Saturday, November 03, 2012
Open Source Next Generation Intrusion Detection and Prevention Engine

The Suricata Engine is an Open Source Next Generation Intrusion Detection and Prevention Engine. This engine is not intended to just replace or emulate the existing tools in the industry, but will bring new ideas and technologies to the field.
OISF is part of and funded by the Department of Homeland Security's Directorate for Science and Technology HOST program (Homeland Open Security Technology), by the the Navy's Space and Naval Warfare Systems Command (SPAWAR), as well as through the very generous support of the members of the OISF Consortium. More information about the Consortium is available, as well as a list of our current Consortium Members.
The Suricata Engine and the HTP Library are available to use under the GPLv2.
The HTP Library is an HTTP normalizer and parser written by Ivan Ristic of Mod Security fame for the OISF. This integrates and provides very advanced processing of HTTP streams for Suricata. The HTP library is required by the engine, but may also be used independently in a range of applications and tools.
- Saba
Posted on Saturday, November 03, 2012
CAINE (Computer Aided INvestigative Environment)
CAINE (Computer Aided INvestigative Environment) is an Italian GNU/Linux live distribution created as a project of Digital Forensics
Currently the project manager is Nanni Bassetti.
CAINE offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface.
The main design objectives that CAINE aims to guarantee are the following:
Currently the project manager is Nanni Bassetti.
CAINE offers a complete forensic environment that is organized to integrate existing software tools as software modules and to provide a friendly graphical interface.
The main design objectives that CAINE aims to guarantee are the following:
- an interoperable environment that supports the digital investigator during the four phases of the digital investigation
- a user friendly graphical interface
- a semi-automated compilation of the final report
Download :- http://www.caine-live.net/page5/page5.html
Posted on Tuesday, October 09, 2012
Cortana Scripts for Armitage
Cortana Scripts
This repository is a collection of Cortana scripts available for your use. Cortana is a scripting language for Armitage and Cobalt Strike.
Click the Downloads link (top right) and download a ZIP or TGZ file with all of the files in this repository. Load what you like.
Tutorial
If you'd like to write your own Cortana scripts, take a look at the Cortana Tutorial. This tutorial also explains how to connect Cortana bots to a collaboration server.
Posted on Tuesday, October 09, 2012
Top 125 Network Security Tools
Top 125 Network Security Tools
We're very impressed by the collective smarts of the security community and we highly recommend reading the whole list and investigating any tools you are unfamiliar with. Click any tool name for more details on that particular application, including the chance to read (and write) reviews. Many site elements are explained by tool tips if you hover your mouse over them. Enjoy!
Posted on Wednesday, September 26, 2012
Ixquick Protects Your Privacy!
Ixquick Protects Your Privacy!
The only search engine that does not record your IP address.
Your privacy is under attack!
Every time you use a regular search engine, your search data is recorded. Major search engines capture your IP
address and use tracking cookies to make a record of your search terms, the time of your visit, and the links you choose - then they store that information in a giant database.
Those searches reveal a shocking amount of personal information about you, such as your interests, family circumstances, political leanings, medical conditions, and more. This information is modern-day gold for marketers,government officials, black-hat hackers and criminals - all of whom would love to get their hands on your private search data.
address and use tracking cookies to make a record of your search terms, the time of your visit, and the links you choose - then they store that information in a giant database.
Those searches reveal a shocking amount of personal information about you, such as your interests, family circumstances, political leanings, medical conditions, and more. This information is modern-day gold for marketers,government officials, black-hat hackers and criminals - all of whom would love to get their hands on your private search data.
Why should you worry?
Major search engines have quietly amassed the largest database of personal information on individuals ever collected. Unfortunately, this data can all too easily fall into the wrong hands. Consider the following story:
In August 2006, the online world was jarred when AOL accidentally releasedthree months' worth of aggregated search data from 650,000 of its users, publishing all the details in an online database.
That database is still searchable. It is an absolute eye-opener to see the potential for privacy nightmares.
In August 2006, the online world was jarred when AOL accidentally releasedthree months' worth of aggregated search data from 650,000 of its users, publishing all the details in an online database.
That database is still searchable. It is an absolute eye-opener to see the potential for privacy nightmares.
Posted on Wednesday, September 26, 2012
Send Private Info That Self-Destructs
Send Private Info That Self-Destructs
Sending confidential information such as passwords, account information and other sensitive data in emails and IM is not necessarily safe. That data is typically stored with remnants of the bits in places you don't need it to be.
_Saba
Posted on Sunday, September 23, 2012
Upload your files anonymously and free on AnonFiles.com
Upload your files anonymously and free on AnonFiles.com.
https://anonfiles.com/
Upload your files anonymously and free on AnonFiles.com.
We offer you hotlinking, 500 MB filesize limit and unlimited bandwidth.
AnonFiles.com is your number one Anonymous File Upload site.
-Saba
https://anonfiles.com/
Upload your files anonymously and free on AnonFiles.com.
We offer you hotlinking, 500 MB filesize limit and unlimited bandwidth.
AnonFiles.com is your number one Anonymous File Upload site.
-Saba
Posted on Sunday, September 23, 2012
ESSPEE - Penetration Testing & Forensics
ESSPEE - Penetration Testing & Forensics
ESSPEE is a derivetive of Back | Track 5, based on Ubuntu 12.04. Designed for users who wish to use only free software. It is packed with featured security tools with stable configurations. This version consolidates the Unity desktop interface; a brand new way to find and manage your applications.
Thanks to Back Track and Blackbuntu for inspiration.
Being a sole developer to this distro, I wish it could help Open Source community with a better interface for Penetration testing and Forensics. I really enjoyed my work for last six months.
Please let me know about bugs and if possible provide solution also.
So finally, "This is the season of roses and wine, this moment is yours....Just live it up !!!"
Features
- A Perfect Forensics Mode - Read-Only Mount
- A Perfect Stealth Mode - Networking Disabled
- Net Activity Viewer - GUI for All Network Connection
- Ruby 1.9.3 - The Latest Available Ruby
- Python 3 +
- Padding Orale Exploit Tool
- Kvirustotal Online Scanning - Scan Suspicious File with File Manager
- Gnome Pie - Press Ctrl+Alt+E and See The Magic
- Babel Enterprise - ISO 27001 Implementation
- Meld - View and Edit the Difference between Two Files or Folders
- MySQL Workbench - MySQL GUI Administration Tool
- OSSEC - System Integrity Monitor
- Linux Kernel 3.4.5-esspee (1000 Hz) Multicore Special
- VMware Player 4.0.4
- Libreoffice 3 with all Plugins
- Penguin Pills - GUI for Multi-Antivirus Products
- Wine QT - A Brand New Interface for Wine Software Managemnet
- FSlint - Duplicate File Finder
- DocFetcher Text Search - Search Words within The Documents
- Tor Browser - Be Anonymous
- Ophcrack GUI


Source and Credit
Posted on Monday, September 10, 2012
Subterfuge Project -Automated Man-in-the-Middle Attack Framework
Posted on Monday, September 10, 2012
Learn Web Design online Free -
Dear friends , I found below useful resource to all. you can learn then free and online. good luck.
All web tutorials @ one place.
Free
Web Templates
|
Tutorials
CSS
Tutorials
Flash
Tutorials
|
Tutorials
HTML
Tutorials
Jquery
Tutorials
|
Tutorials
Ajax
Tutorials
PHP
Tutorials
|
Tutorials
Java
Script Tutorials
Galleries
|
Posted on Saturday, September 08, 2012
Subscribe to:
Posts (Atom)